WannaCry: What is Ransomware and How to Avoid it?
Everyone remembers the incident of October 21, 2016. Distributed Denial of Services (DDOS) attacked a US company Dyn. This was the biggest cyber attack until Friday 12th of May, 2017. A malicious software WannaCry infected 200,000 computers in over 150 countries. It is typically a Ransomware.
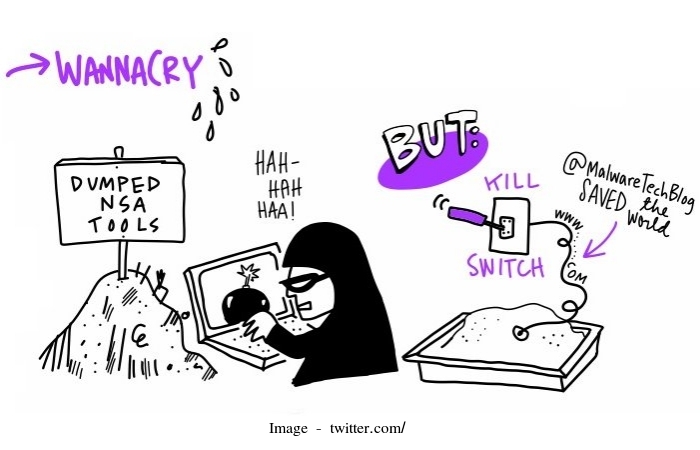 The “Accidental Hero” who halted the global digital catastrophe by registering a scramble domain name hidden in the malware warned again that the hackers can reboot again.
Everything was distorted, Companies like FedEx and Telefonica wrecked. Even the UK’s National Health Services (NHS) weren’t operational. The surgeries were canceled, as the patient’s records and other important files were unavailable.
In this chaos was all of a sudden halted when one UK cyber security researcher who tweets as @malewaretechblog found a kill switch in the malicious software.
The “Accidental Hero” who halted the global digital catastrophe by registering a scramble domain name hidden in the malware warned again that the hackers can reboot again.
Everything was distorted, Companies like FedEx and Telefonica wrecked. Even the UK’s National Health Services (NHS) weren’t operational. The surgeries were canceled, as the patient’s records and other important files were unavailable.
In this chaos was all of a sudden halted when one UK cyber security researcher who tweets as @malewaretechblog found a kill switch in the malicious software.
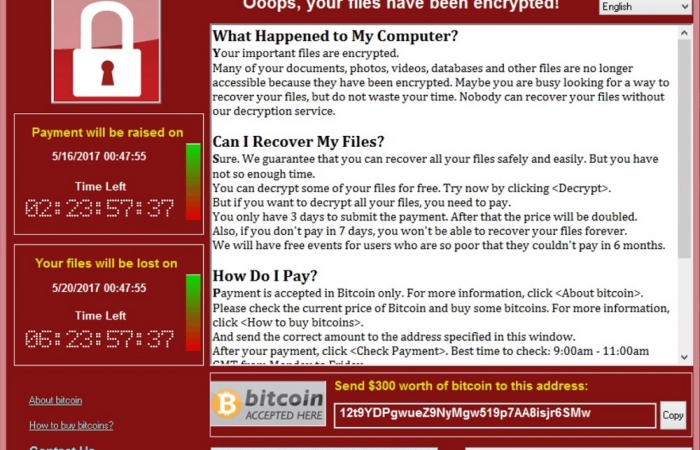 The ransomware was WannaCry. It encrypts your Hard drive and then ask for a ransom of $ 300 worth of cryptocurrency Bitcoin. Europol declared the malicious software "lame" as there was only 4 bitcoin address were hardcoded. This will certainly make the tracking a lot easier.
Also, some cyber security researcher proclaimed this attack as a catastrophic failure as even with such a huge spread these attacks generated only $55,000 which is significantly low.
Ransomware is quite in trend for last two years and possibly the biggest threat present in terms of cyber attacks. It is a malicious software which will encrypt the files on your computer and gives you few days to pay some amount of money or else it will delete every single data present on your computer. It is just like asking for money through extortion.
Ransomware is a problem that can scare the hell out of you. However, there is no need for panic as I will give all the in-depth information of this god’s forbidden hacker’s gizmo.
The ransomware was WannaCry. It encrypts your Hard drive and then ask for a ransom of $ 300 worth of cryptocurrency Bitcoin. Europol declared the malicious software "lame" as there was only 4 bitcoin address were hardcoded. This will certainly make the tracking a lot easier.
Also, some cyber security researcher proclaimed this attack as a catastrophic failure as even with such a huge spread these attacks generated only $55,000 which is significantly low.
Ransomware is quite in trend for last two years and possibly the biggest threat present in terms of cyber attacks. It is a malicious software which will encrypt the files on your computer and gives you few days to pay some amount of money or else it will delete every single data present on your computer. It is just like asking for money through extortion.
Ransomware is a problem that can scare the hell out of you. However, there is no need for panic as I will give all the in-depth information of this god’s forbidden hacker’s gizmo.
 A ransomware is a typical malicious malware, which blocks the access of the victims to the files and folder (Generally the whole computer) and it requires a decrypting key to unblocking the blocked content. The hacker demands for ransom in exchange for the key. This is why it got this name, "Ransomware".
A ransomware is a typical malicious malware, which blocks the access of the victims to the files and folder (Generally the whole computer) and it requires a decrypting key to unblocking the blocked content. The hacker demands for ransom in exchange for the key. This is why it got this name, "Ransomware".

 Well, they are the most vulnerable users. And why is that, go through the points below and you will know for yourself,
Well, they are the most vulnerable users. And why is that, go through the points below and you will know for yourself,
 Business may not be that much vulnerable, however, the real money is in business. So, let’s have a look at the points,
Business may not be that much vulnerable, however, the real money is in business. So, let’s have a look at the points,
 Many of us depend totally over to antivirus software, however, ransomware usually remains covert in the presence of an antivirus.
Let’s see, what kind of tactics does this malware apply to remain undetected even in the presence of an antivirus.
Many of us depend totally over to antivirus software, however, ransomware usually remains covert in the presence of an antivirus.
Let’s see, what kind of tactics does this malware apply to remain undetected even in the presence of an antivirus.
 Before going straight to the solution, I want you to make a vow that you’ll take this ransomware problem seriously and will do something about it before that wave hit you and your data.
Now, all these steps are for PC (locally) I want you to do,
Before going straight to the solution, I want you to make a vow that you’ll take this ransomware problem seriously and will do something about it before that wave hit you and your data.
Now, all these steps are for PC (locally) I want you to do,
Ransomware Hit 200,000 Victims in Over 150 Countries
It was Friday 12th of May, 2017, a wave of cyber attack hit in over 150 countries and infected 200,000 victims (Still rising). Europol Director Rob Wainwright quoted the attack as indiscriminate. Wainwright further quoted these attacks as unique because if one computer in a network gets affected, the infection spread through the entire network. He added few banks in Europe had been affected, as they know the pain of being the number 1 target of cyber criminals. “We have been concerned for some time that the healthcare sectors in many countries are particularly vulnerable. They're processing a lot of sensitive data,” He added. Wainwright said Europol is now working with US agency FBI in order to track down the personnel responsible for this mayhem. Also read: 11 Ways to Secure Website in Just 15 Minutes‘Accidental Hero’ Who Saved Us All
 The “Accidental Hero” who halted the global digital catastrophe by registering a scramble domain name hidden in the malware warned again that the hackers can reboot again.
Everything was distorted, Companies like FedEx and Telefonica wrecked. Even the UK’s National Health Services (NHS) weren’t operational. The surgeries were canceled, as the patient’s records and other important files were unavailable.
In this chaos was all of a sudden halted when one UK cyber security researcher who tweets as @malewaretechblog found a kill switch in the malicious software.
The “Accidental Hero” who halted the global digital catastrophe by registering a scramble domain name hidden in the malware warned again that the hackers can reboot again.
Everything was distorted, Companies like FedEx and Telefonica wrecked. Even the UK’s National Health Services (NHS) weren’t operational. The surgeries were canceled, as the patient’s records and other important files were unavailable.
In this chaos was all of a sudden halted when one UK cyber security researcher who tweets as @malewaretechblog found a kill switch in the malicious software.
“I was out having lunch with a friend and got back about 3 pm and saw an influx of news articles about the NHS and various UK organizations being hit,” he told the Guardian. “I had a bit of a look into that and then I found a sample of the malware behind it, and saw that it was connecting out to a specific domain, which was not registered. So I picked it up not knowing what it did at the time.”MalwareTech elaborates the kill switch was hard coded in the software in case the creator wants to stop the spread. This complex process involves a lengthy absurd domain name. He bought that domain just to monitor the spread, but eventually or I prefer saying accidentally hit the “kill switch” and put an end to this chaos. The kill switch certainly stops the further spreading of this malicious software. This kill switch did no good for already infected computers.
WannaCry: Catastrophic Failure!!!
 The ransomware was WannaCry. It encrypts your Hard drive and then ask for a ransom of $ 300 worth of cryptocurrency Bitcoin. Europol declared the malicious software "lame" as there was only 4 bitcoin address were hardcoded. This will certainly make the tracking a lot easier.
Also, some cyber security researcher proclaimed this attack as a catastrophic failure as even with such a huge spread these attacks generated only $55,000 which is significantly low.
Ransomware is quite in trend for last two years and possibly the biggest threat present in terms of cyber attacks. It is a malicious software which will encrypt the files on your computer and gives you few days to pay some amount of money or else it will delete every single data present on your computer. It is just like asking for money through extortion.
Ransomware is a problem that can scare the hell out of you. However, there is no need for panic as I will give all the in-depth information of this god’s forbidden hacker’s gizmo.
The ransomware was WannaCry. It encrypts your Hard drive and then ask for a ransom of $ 300 worth of cryptocurrency Bitcoin. Europol declared the malicious software "lame" as there was only 4 bitcoin address were hardcoded. This will certainly make the tracking a lot easier.
Also, some cyber security researcher proclaimed this attack as a catastrophic failure as even with such a huge spread these attacks generated only $55,000 which is significantly low.
Ransomware is quite in trend for last two years and possibly the biggest threat present in terms of cyber attacks. It is a malicious software which will encrypt the files on your computer and gives you few days to pay some amount of money or else it will delete every single data present on your computer. It is just like asking for money through extortion.
Ransomware is a problem that can scare the hell out of you. However, there is no need for panic as I will give all the in-depth information of this god’s forbidden hacker’s gizmo.
For a secure website that generates business, contact Wordsuccor
What is Ransomware?
 A ransomware is a typical malicious malware, which blocks the access of the victims to the files and folder (Generally the whole computer) and it requires a decrypting key to unblocking the blocked content. The hacker demands for ransom in exchange for the key. This is why it got this name, "Ransomware".
A ransomware is a typical malicious malware, which blocks the access of the victims to the files and folder (Generally the whole computer) and it requires a decrypting key to unblocking the blocked content. The hacker demands for ransom in exchange for the key. This is why it got this name, "Ransomware".
The Ransomware are generally of two types-
1. Encryptors
This software contains sophisticated encryption algorithms. These algorithms blocks the system files. They simply ask for money in return of decryption key. CryptoWall is an example of Encryptors.2. Lockers
It tends to lock the victim out of the operating system. As a result, all the apps and files are impossible to access, even the desktop. The files are simply locked and the hacker simply ask for ransom to open the files. Winlocker is a perfect example of Locker's.3. Versions of Lockers
It which tends to infect MBR (Master Boot Record). So, MBR is the reason a PC can reboot. When a ransomware infects the record, instead of booting, it shows a ransom note. Satana families are exactly similar lockers.Why is Ransomware Different from other Malware?

- The ransomware possesses unbreakable encryption.
- A ransomware can encrypt every type of file including documents, images, videos, pdfs, audio etc.
- Ransomware easily modify your file names. After this you will have nno idea about your files and its location.
- A ransomware will add a different extension to the file to give a certain amount of ransomware strain.
- A ransomware asks for for money in Bitcoins. Bitcoins are not easy to track.
- The ransomware have a time-frame. After the time limit, the ransom money will increase. and ultimately deletion of your files.
- It follows a certain set of delusion techniques which is undetectable by traditional antivirus.
- Encryption is not always the end game. They can also send tangible and volatile data like bank details, credit card details etc to a cybercrime syndicate. With them on your device, anything is possible.
- They can also target geographically. This also means that they can let you know through a ransom note written in your native language which gives them psychological leap over you.
Our experienced WordPress developers use advanced security tools to prevent websites from threats and risks.
Why Ransomware Attacks Home User?
 Well, they are the most vulnerable users. And why is that, go through the points below and you will know for yourself,
Well, they are the most vulnerable users. And why is that, go through the points below and you will know for yourself,
- They usually have no data backup. Nobody takes it seriously.
- They used to click almost everything as they have either little or no knowledge about the cyber security.
- Most of the time they lack even the most basic line of security.
- They tend to ignore software updates.
- Almost all home users depend on antivirus for protection which is quite ineffective on ransomware.
Why Ransomware Attacks Businesses?
 Business may not be that much vulnerable, however, the real money is in business. So, let’s have a look at the points,
Business may not be that much vulnerable, however, the real money is in business. So, let’s have a look at the points,
- As it includes a huge pile of cash, that’s why hacker attacks businesses.
- There are more chances of getting money if a successful infection penetrates to cause major business disruption.
- Also, the computer systems are complex and vulnerable to such attacks.
- With some basic social engineering tacts, one can take advantage to prey on the human factor.
- Ransomware can easily penetrate deep not only into computers but also on servers and cloud-based file sharing system.
- Cyber criminals also aware of the facts that big businesses will not report these kinds of activities because it might ruin their brand value.
Our custom WordPress development services ensure 24/7 support to keep your website secure!
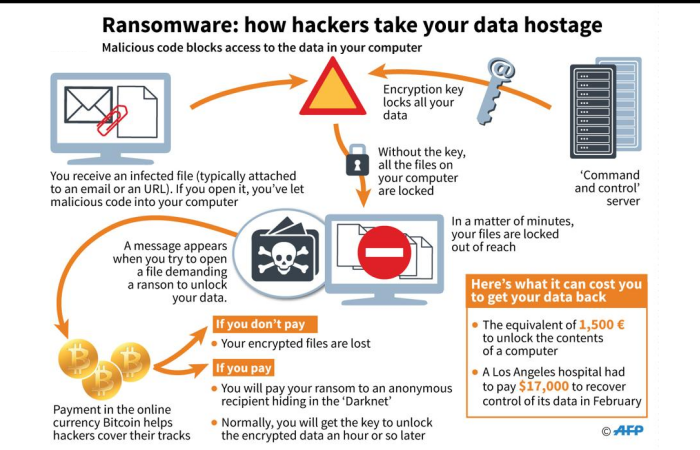
How Ransomware Infection Occur?

Image source - dailymail.co.uk/
The process of such infection is simple which is why it is more dangerous. Have a look on the steps describing how an infection occur,- At the outset, the victim receives a spam mail, with malicious link or attachment. It can also create a back door if the victim has visited any website to download the malicious software.
- The targeted PC will receive a payload if the victim clicks the link or attachment.
- The downloader utilizes the list of C&C servers controlled by the villain hackers in order to download the ransomware software.
- This malware then encrypts the entire hard disk content. Everything, including cloud data sync on the PC.
- And at last a warning pop up on the screen asking for ransom and how to pay the ransom for the decryption appears.
How the ransomware threat spread?
The cyber criminals always look for the easiest way to infect a system or network and they tend to use that as a backdoor to spread the malevolent content. These are some common methods adopted by these villain hackers,- Spam Email campaign.
- Loopholes in the security of a software.
- Online traffic redirects to malicious software.
- Malevolent script injection on legitimate websites.
- Self-propagation.
- Botnets.
- Drive-by downloads.
Why Ransomware goes Undetected by an Antivirus?
 Many of us depend totally over to antivirus software, however, ransomware usually remains covert in the presence of an antivirus.
Let’s see, what kind of tactics does this malware apply to remain undetected even in the presence of an antivirus.
Many of us depend totally over to antivirus software, however, ransomware usually remains covert in the presence of an antivirus.
Let’s see, what kind of tactics does this malware apply to remain undetected even in the presence of an antivirus.
- The communication with the control and command servers are encrypted and hard to detect in network traffic.
- It also features built-in traffic proxies like Bitcoin, which eliminates the tracking by any law enforcement agency.
- Anti-sand box mechanism is utilized which are hard to pick by an anti virus.
- Domain shadowing hides the communication between the payload and the servers controlled by the villain hackers.
- With Fast flux, the source of the infection remains anonymous.
- Another trick it plays is the deployment of encrypted payloads which remains undetected by an antivirus.
10 Ways that will Take your Ransomware Security to the Next Level
 Before going straight to the solution, I want you to make a vow that you’ll take this ransomware problem seriously and will do something about it before that wave hit you and your data.
Now, all these steps are for PC (locally) I want you to do,
Before going straight to the solution, I want you to make a vow that you’ll take this ransomware problem seriously and will do something about it before that wave hit you and your data.
Now, all these steps are for PC (locally) I want you to do,
- Do not store any important data on your PC (Sometimes it is difficult but you have to do that)
- Make 2 backups of your data, one on external hard drive and other in the cloud- Dropbox/Google drive.
- Do not let the Google Drive or Dropbox on throughout the day, just open it once or twice a day to sync the data.
- Keep your Operating System and all other software are up to date. If not, it is time to update them all.
- For daily use, make a guest account with limited access. Do not use administration account on daily basis.
- Turn off the macros in the Microsoft Office suite in the browser.
- Remove all the plugins like Adobe Flash or Reader from the browser. Set the setting to ask before use.
- Remove outdated Plugins and add-ons, do not keep unnecessary plugins and add-ons.
- Adjust your browser’s security and privacy setting up to highest.
- Use an ad-blocker to block all the malicious advertisements.





